Motivation ...
Attacking server systems turned into a kind of new "public sports" during the last 5 years.
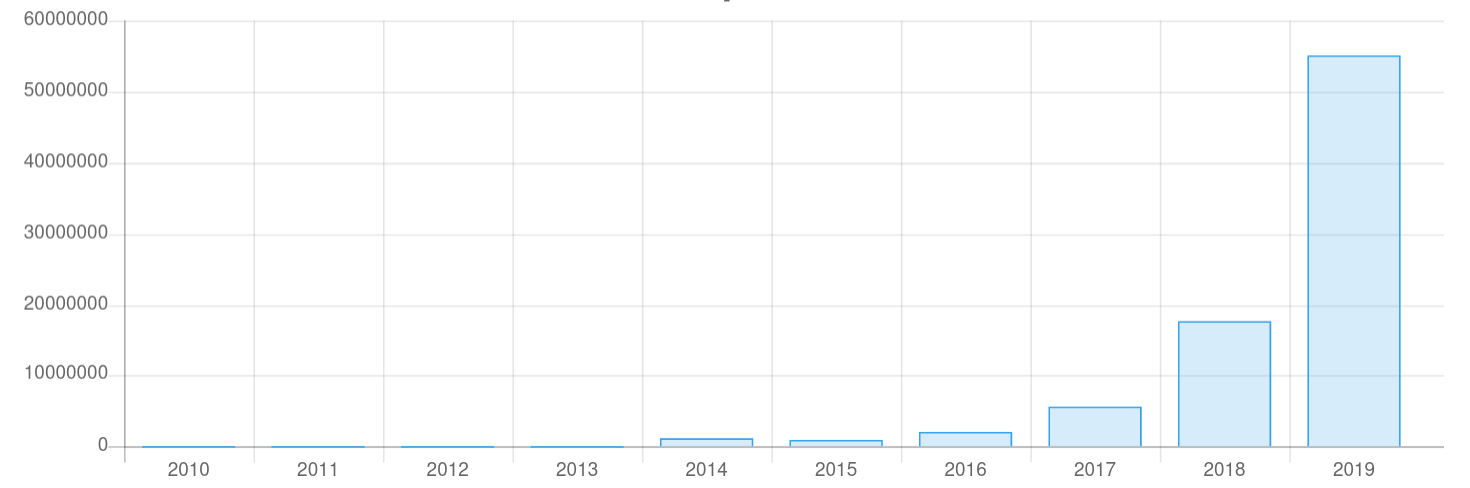
From 2015 until end of 2019 the reported numbers of malicious IP addresses that are attacking server systems on the open Internet has grown from about 1 million to 55 million attacks identified by IP addresses that makes up an increase of about 300% by every year.
This is exponential grows ...
The majority of attacks goes into account of mail services (mail transport & mailbox access; ~60%) followed by console access services (login/sshd; ~25%). The remaining 15% go into account of other services like chiefly WEB services and other informational services.
Spreaders of SPAM, SCAM & Phishing email etc. earn about 10 to 15 thousands US dollars per week and a number of 2005 says, that 5.4 billion US dollars were made with spreading SPAM - 15 years ago ... todays numbers can be expected tremendously higher.
In 2020 the reported number of server attacks "only" doubled to ~118 billion compared to ~56 billion in year 2019 ...
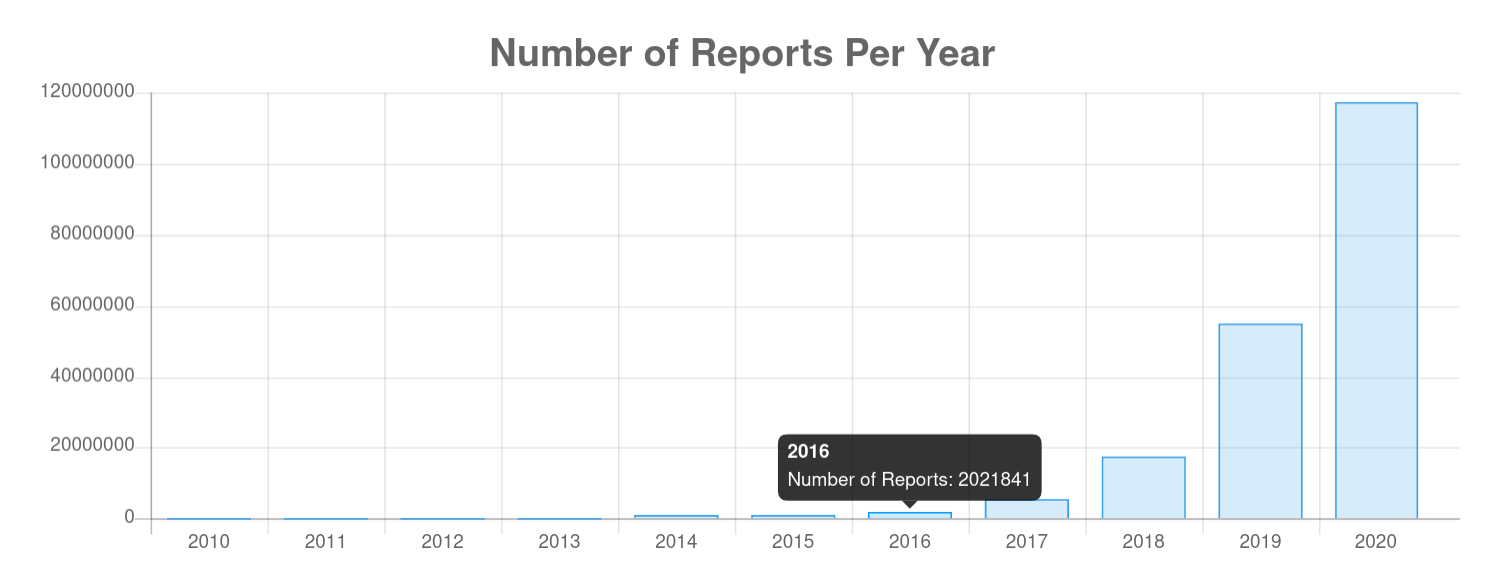
... but the "quality" by which internet bandits conduct their attacks has increased as well.
The remedy ... Detect and react ...
The only effective counter measure is a realtime intrusion detection system (RIDS) with instant measure by firewall DROPs to get attacking IP addresses under control before these can mess with the services on a server system. Nowadays attackers have 'tools' to deploy brute-force-attacks that can fire over 20 attacks per second against a server system. With 'traditional' log file scanning it is not even closely possible to detect such an aggressive behavior ... not to speak of the defense ...
Watcher fills your firewall lightning-fast at machine start-up or after reboot from:
- Static lists (individual blacklists and a whitelist; manually maintained)
- DynLoaders (from common and reliable public resources like 'SpamHaus' & 'NixSpam'; Dynloaders for SpamHaus & NixSpam are included with the master-package at no charge. Instructions on how you can build your individual dynloader can be found in the Watcher-Master manual.
Watcher modules are available for:
- Login [sshd]
- Mail transport [MTA] & Mailbox access [POP, IMAP],
- WEB SERVER [httpd]
Modules are working fully dynamic and provide intrusion detection & prevention in real-time. The attacking events are tracked and stored in the exclusive databases of each module for rapid retrieval with predictable processing times.
Modules are dynamically fed by the system logger (rsyslog or syslog-ng). The modules analyse logging messages in real-time, keep track of attackers in databases and feed the firewall autonomously with DROPs as 'bandits' reach configurable limits of attacking your server system.